Understanding and Defend Against DOS & DDOS Attacks
In today’s evolving cyber world, protecting your online presence is crucial. Network security is a priority due to the constant evolution of web threats. Among these, DOS (Denial of Service) and DDOS (Distributed Denial of Service) attacks are highly damaging. These cyberattacks disrupt usual online activities by overwhelming networks with excessive traffic. In this blog, we will explore the ins and outs of DOS and DDOS attacks, how they work, what is the possible impact due to these attacks and what are the defense measures against them.
What is a Denial of Service (DOS) Attack?
A DOS attack is a malicious attempt to crash or severely slow down a targeted network or system by overwhelming it with a flood of illegitimate traffic or requests. This can render the network or system completely inaccessible to users, causing anything from minor inconvenience to severe financial or reputational losses. DOS attacks can be executed in several ways, such as sending a massive number of requests to a server, overloading the server’s capacity, and causing it to crash, or exploiting system vulnerabilities to take control.
The first DoS attack was discovered in 1974 by a group of researchers during their testing of ARPANET, a precursor to the modern-day Internet. The researchers sent various packets to the Network Measurement Center at the University of Southern California, which caused the system to crash.
See below detailed DoS attack types
SYN Flood Attack
A SYN flood attack involves overwhelming a server by sending numerous TCP SYN packets. The server initiates a 3-way handshake, but the attacker ignores SYN-ACK replies, exhausting server resources and causing service disruption.
UDP Flood Attack
A UDP Flood attack occurs when an attacker sends numerous UDP packets to a target server, usually with a spoofed source IP Address, causing it to be overwhelmed and resulting in a denial of service. This type of attack aims to disrupt and exhaust server resources.
Ping Flood Attack
A Ping Flood attack occurs when a malicious user sends a bunch of ICMP echo request packets (ping) to the targeted server, overwhelming its resources and potentially causing it to become unresponsive.
HTTP Flood Attack
An HTTP Flood attack overwhelms a target’s server by sending massive HTTP requests, consuming resources & bandwidth, leading to server unresponsiveness, following attack is used to the disrupt the target’s functionality by exploiting web server limitations.
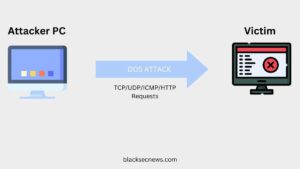
Distributed Denial of Service (DDOS) Attack.
A DDOS attack is similar to a DOS attack, but with one key difference it uses multiple sources, often compromised devices such as computers, smartphones, and IoT devices, to flood the target network with an enormous volume of traffic simultaneously. This distributed approach makes DDOS attacks much harder to deflect or trace back to their origin. DDOS attacks can be particularly devastating, as they can bring down entire networks, disrupt services and communications, and cause significant financial and reputational damage to the targeted organization.
As mentioned, DDOS Attack is similar to DoS attack, and it uses the same attack path as described above.
See below DDOS Attack example.
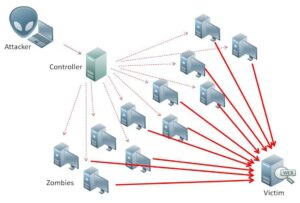
The Impact of DOS and DDOS Attacks
DOS and DDOS attacks can have a wide range of effects on targeted networks, systems, and organizations. These include, but are not limited to:
Inaccessibility of resources: As mentioned earlier, DOS and DDOS attacks can cause a network or system to crash or become severely impaired, preventing legitimate users from accessing online resources or services.
Financial losses: Depending on the nature of the targeted organization, a DOS or DDOS attack can cause considerable financial losses, such as lost sales, compensation to affected customers, or even contractual penalties.
Reputational damage: DOS and DDOS attacks can cause harm to an organization’s reputation, leading to a potential loss of customers, investors, or partners.
Increased IT costs: Dealing with the aftermath of a DOS or DDOS attack often requires additional resources and personnel to assess, mitigate, and repair the damage, leading to increased IT costs.
Legal and regulatory consequences: In some cases, organizations that experience data breaches or other consequences due to a DOS or DDOS attack may face legal or regulatory penalties.
Preventing DOS & DDOS Attacks Steps You Can Take
While no single solution can guarantee complete protection against DOS and DDOS attacks, there are several steps you can take to reduce the likelihood and potential impact of such attacks:
Implement strong security measures: Ensure that your systems and networks have robust security features in place, such as firewalls, intrusion prevention systems, and regular vulnerability scans.
Monitor traffic patterns: Continuous monitoring of traffic patterns can help you detect unusual activity, such as sudden spikes or surges in incoming traffic, which may indicate an ongoing DOS or DDOS attack.
Use an anti-DDOS service: Many cybersecurity service providers offer specialized anti-DDOS services that can help detect, mitigate, and block DDOS attacks before they cause significant harm.
Ensure proper bandwidth management: Properly allocating bandwidth to different services and prioritizing legitimate traffic can help mitigate the effects of a DOS or DDOS attack on your network.
Regularly update and patch your systems: Keeping your systems and software up-to-date and applying security patches as soon as they are released can help protect against potential DOS and DDOS attacks that exploit vulnerabilities.
Strengthening Your Defense, A Collaborative Effort
Fighting against DOS and DDOS attacks requires not just robust network security measures but also a strong cybersecurity culture within your organization. This includes ongoing employee training on cybersecurity best practices, establishing clear policies and procedures for identifying and reporting suspected cyberattacks, and fostering a collaborative environment where everyone plays a role in protecting the organization from cyber threats.
The future of DoS and DDOS Attacks
The future of DoS and DDoS attacks may see hackers using smarter tactics and leveraging a higher number of IoT devices to flood targeted systems. These attacks could disrupt essential services by overwhelming networks with data, preventing regular users from accessing the services. Hackers might even mix various attack methods to confuse defenses and hide their tracks more effectively. On the other hand, cybersecurity experts are working on developing stronger protection measures using AI and machine learning to better detect and combat such threats. Overall, the battle between attackers and defenders will continue to intensify, but advanced tools will help keep our digital world safer.
Largest DDoS Attacks
Large scale DDOS Attack against GitHub
In 2018, GitHub, a widely used website for sharing computer code by software developers, faced a massive DDoS attack. GitHub’s case, the attack was huge, reaching 1.35 terabits per second (Tbps) at its highest peak point. This is like millions of people visiting a website at the same time, making it unable to cope with the pressure. The attack lasted for about 20 minutes. Thankfully Akamai Prolexic stepped in and helped stop the attack. They worked to make sure GitHub could handle the extra traffic and remain up and running.
The Dyn Attack
In October 2016, a huge cyber-attack happened. It aimed at Dyn, a company which provides DNS services for company websites like Twitter, Netflix, and Amazon. The attack was done using Mirai Botnet. It was very strong, reaching 1.2 Tbps a record at that time. This caused problems for many people to access their services.
Spam house Attack
In March 2013, Spamhaus, a non-profit organization which provides backlist service and provides service to detect spam emails was targeted by a massive DDoS attack that peaked at 300 gigabits per second Gbps .Attack was carried out using a botnet of compromised servers and was one of the largest at the time.
Conclusion
DOS and DDOS attacks pose a significant risk to network security, often causing devastating effects on targeted systems and organizations. By understanding the nature of these attacks, their potential impacts, and the measures that can be taken to prevent them, individuals and organizations can take crucial steps towards ensuring the security and integrity of their online presence. Remember that the adage “an ounce of prevention is worth a pound of cure” holds especially true when it comes to DOS and DDOS attacks—appropriate measures and continuous vigilance are essential to safeguarding your digital assets.
Free Resources to Mitigate DOS & DDOS Attacks
1. Cloudflare Glogbal CDN Network which offers free plan for to protect your servers or website.
2.Akamai also well known security provider which provides few free and low cost services to against DDOS Attacks
3.fail2ban and Iptables to block known malicious IP Addresses
4.Open source firewalls such as pfSense and Untangle to filter unwanted traffic



