What is the OSI Model?
What is the OSI Model?
Have you ever heard of the OSI model and struggled to understand exactly what it is? Comprehending the OSI model is a fundamental step for anyone wanting to gain an understanding of cybersecurity. The OSI (Open Systems Interconnection) model is a conceptual framework for computer network communications that divides how data travels between devices into seven distinct layers. In this blog post, we’ll explore each layer in-depth so as to provide an extensive guide on what exactly the OSI model involves and why it’s considered such an important part of our digital infrastructure.
What is the importance of the OSI model in computer networking?
The OSI model is a crucial conceptual framework for computer networking that organizes network communication into seven layers. This standardization is essential because it enables seamless communication between devices, regardless of manufacturer or operating system. The OSI model simplifies network design and troubleshooting, allowing for more efficient problem-solving, and is a cornerstone of modern computer networks. Anyone interested in cybersecurity should have a working knowledge of the OSI model and its principles.
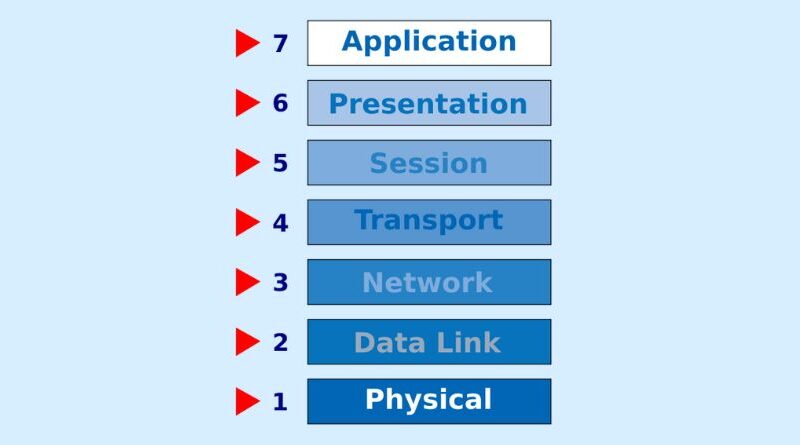
The OSI model consists of seven layers, each of which handles a different task in the process of transmitting data from one device to another. These seven layers are
7.Application Layer
The seventh layer of the OSI (Open Systems Interconnection) Model is the Application Layer. This layer serves as an interface between the user and the network, allowing users to access applications and services on the network. It is responsible for providing user-friendly access to network resources while ensuring data security. The most common application protocols used in this layer are Hypertext Transfer Protocol (HTTP), File Transfer Protocol (FTP), Simple Mail Transfer Protocol (SMTP), and Telnet.
These protocols provide access to remote systems, file transfer, email, and command line control over networks. Additionally, several application layer functions involve establishing sessions or connections between computers or devices on a network, such as VoIP (Voice over Internet Protocol). Finally, this layer also helps in authenticating users by verifying their identity prior to granting access to certain applications or services.
6.Presentation Layer
Presentation Layer of the OSI model is responsible for making sure that the data sent from one application to another is in the correct format so that it can be processed. It does this by providing a layer of abstraction between the applications and the network, allowing them to communicate without understanding each other’s underlying protocols. The most common protocols used at this layer include MPEG, JPEG, GIF, MIDI and TIFF.
At this layer, various tasks such as encryption/decryption, compression/decompression, character code translation and data conversion are performed. This allows different types of systems to communicate with each other despite having different hardware or software specifications. For example, a Macintosh computer can easily send documents for printing on a Windows-based printer if both use an appropriate presentation protocol like Postscript or PDF. Additionally, the Presentation Layer also performs authentication tasks to ensure that only legitimate users are allowed access to a system’s resources.
5.Session Layer
The fifth layer of the OSI Model is the Session Layer. This layer is responsible for establishing, maintaining, and managing communication sessions between two applications. It consists of protocols that create, manage and terminate communication sessions. This layer also provides a mechanism for error recovery and devices to detect if one end of the session has stopped responding. It helps applications exchange data in an orderly fashion by creating dialogs or virtual connections between application processes to synchronize activities. Furthermore, it enables multiplexing of multiple application conversations over a single physical connection so that each conversation can take place independently on its own channel.
Additionally, it ensures proper sequencing of data transmitted among different nodes and tracks the state of each session from one transmission to the next. Session layer services provide conveniences like allowing files to be transferred in segments rather than all at once, making sure errors don’t occur during file transfers and keeping track of the progress while transferring large files with various techniques such as windowing protocols.
4.Transport Layer
The OSI Model Transport Layer is responsible for reliable data transmission between two endpoints, as well as segmentation and reassembly of large amounts of data. It provides end-to-end transport services, which are based on the services offered by the lower network layer. Common protocols within the Transport Layer include TCP (Transmission Control Protocol), UDP (User Datagram Protocol) and SPX (Sequenced Packet Exchange).
The primary function of these protocols are to ensure reliable communication between hosts in a network by providing error checking, connection setup, flow control and sequencing of data packets. Additionally, each protocol defines its own type of segmenting and reassembling mechanism to further facilitate communication over unreliable networks. For example, TCP uses a window-based approach for segmentation and reassembly while UDP utilizes a datagram approach. Ultimately, Layer 4 plays an essential role in maintaining reliable communication by ensuring that data packets reach their destination in an orderly fashion without any corruption or losses.
3.Network Layer
Network Layer is responsible for routing and switching of network data packets. It determines the best path for data transmission across an interconnected network and serves as an interface between the physical layer and the higher layers of the model. Additionally, this layer defines addressing schemes in order to identify nodes within a network. Common protocols used at this layer include IP (Internet Protocol), ICMP (Internet Control Message Protocol), ARP (Address Resolution Protocol), RARP (Reverse Address Resolution Protocol) and IGMP (Internet Group Management Protocol).
These protocols allow for the segmentation of data into smaller chunks known as datagrams, which are then routed through intermediate networks until they reach their intended destination. Furthermore, Layer 3 also provides error notification services so that any issues can be quickly detected and resolved. As such, this layer plays a key role in ensuring reliable communication between two or more endpoints on a network.
2.Data Link Layer
Data Link Layer is responsible for providing reliable and efficient data transmission across physical networks. It provides the functionality to establish and maintain a link between two nodes. It also handles error detection and correction, as well as flow control to ensure that data is not lost during transmission. Furthermore, it provides the means to logically organize data frames into packets of binary information. With this layer, devices are able to identify and address each other in order to transfer data.
The Data Link Layer offers various technologies such as Media Access Control (MAC) addressing, Token Ring protocol for local area networks (LANs), Local Area Network Bridging (LAN B), Ethernet, Point-to-Point Protocol (PPP) for connecting computers on the Internet, Virtual LANs (VLANs) for grouping hosts together regardless of physical location. Therefore, it serves as the keystone of all communication protocols in local area networks, enabling devices connected to a network to communicate with each other securely and reliably.
1.Physical Layer
Physical Layer is responsible for the physical transmission of data between two devices. It defines the physical characteristics, such as electrical and mechanical interfaces, signal types and levels, and how to move information across a link. This layer is also responsible for electrical and mechanical specifications of interfaces, as well as the modulation and transmission technique used.
Apart from providing an interface between the Data Link layer (Layer 2) and the actual physical medium, this layer is also responsible for error correction or detection. This layer consists of components such as connectors, hubs, repeaters and transceivers which handle various aspects of transmitting data through a media. Examples of protocols at this level are Ethernet over copper cables or Wi-Fi over radio waves.
Conclusion
The OSI model is a conceptual framework that standardizes the communication process between networked devices by breaking it down into seven distinct layers each with its own responsibilities. Understanding how each layer works can help you troubleshoot problems more easily and develop new networking technologies. Additionally, using the OSI model as a reference when designing or modifying protocols can be extremely helpful. Thanks for reading!